1.查壳
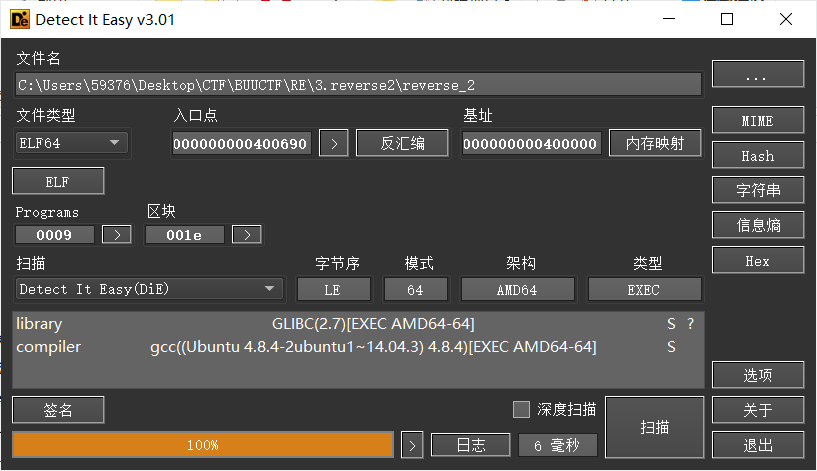
ELF64 无壳
kali中运行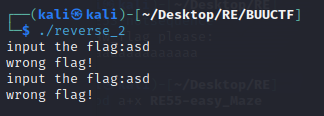
用户输入两次flag,程序验证后输出提示,程序退出
2.IDA静态分析
main:
int __cdecl main(int argc, const char **argv, const char **envp)
{
int stat_loc; // [rsp+4h] [rbp-3Ch] BYREF
int i; // [rsp+8h] [rbp-38h]
__pid_t pid; // [rsp+Ch] [rbp-34h]
char s2[24]; // [rsp+10h] [rbp-30h] BYREF
unsigned __int64 v8; // [rsp+28h] [rbp-18h]
v8 = __readfsqword(0x28u);
pid = fork();
if ( pid )
{
waitpid(pid, &stat_loc, 0);
}
else
{
for ( i = 0; i <= strlen(&flag); ++i )
{
if ( *(&flag + i) == 'i' || *(&flag + i) == 'r' )// 数组flag为:{hacking_for_fun}
*(&flag + i) = '1'; // 替换后为:{hack1ng_fo1_fun}
}
}
printf("input the flag:");
__isoc99_scanf("%20s", s2);
if ( !strcmp(&flag, s2) )
return puts("this is the right flag!");
else
return puts("wrong flag!");
}与上题思路一样,将数组flag中的"i"和"r"替换为"1"即可得到flag
到程序中验证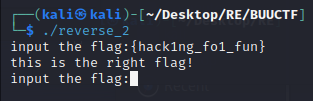
flag为:flag{hack1ng_fo1_fun}