一、查看文件类型
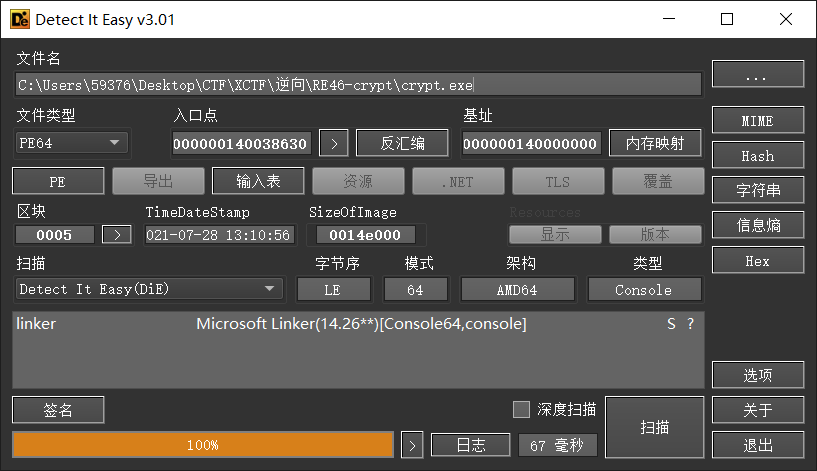
PE64 无壳
运行
无提示信息,直接输入后回车,程序退出
二、IDA静态分析
1.查看main函数

输入的字符串进行一系列加密处理后,最终与0x22进行循环异或,再与题目所给数组进行比较,若一致则输出正确提示
题目所给数组提取为:
unsigned char ida_chars[] =
{
0x9E, 0xE7, 0x30, 0x5F, 0xA7, 0x01, 0xA6, 0x53, 0x59, 0x1B,
0x0A, 0x20, 0xF1, 0x73, 0xD1, 0x0E, 0xAB, 0x09, 0x84, 0x0E,
0x8D, 0x2B
};
2.查看sub_140001120
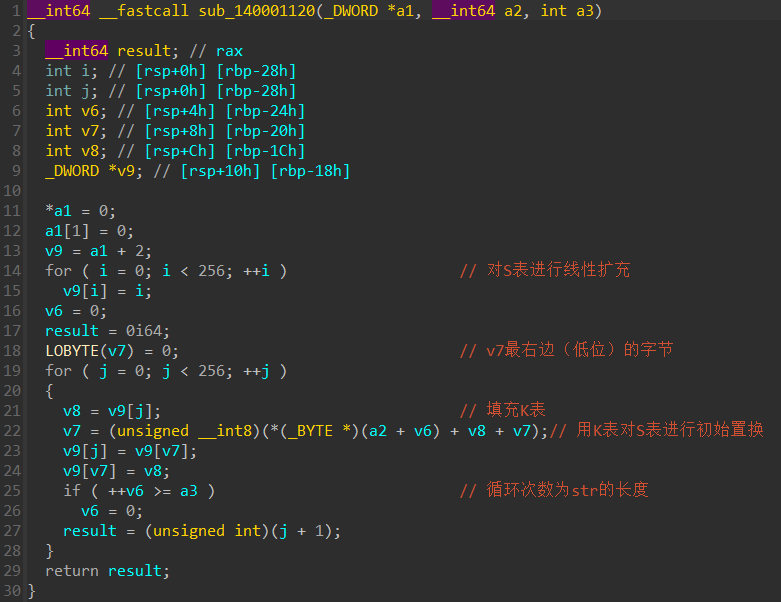
阅读代码后发现符合RC4算法的特征运算
判断此函数为S盒变换
3.查看sub_140001240
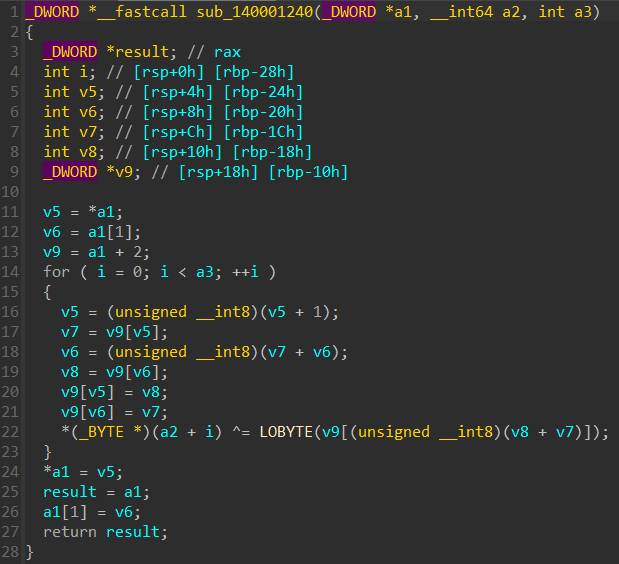
此函数为密钥流生成,以及密钥流与明文异或
三、解题
RC4为对称加密算法,故对密文再次进行加密即可
(1)先将题目所给数组与0x22进行循环异或,并以字节流输出,得到密文。
脚本如下:
res=[
0x9E, 0xE7, 0x30, 0x5F, 0xA7, 0x01, 0xA6, 0x53, 0x59, 0x1B,
0x0A, 0x20, 0xF1, 0x73, 0xD1, 0x0E, 0xAB, 0x09, 0x84, 0x0E,
0x8D, 0x2B ]
flag=[]
for i in range(len(res)):
flag.append(res[i]^0x22) print(bytes(flag))
运行结果为: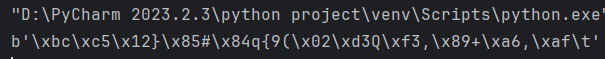
b'\xbc\xc5\x12}\x85#\x84q{9(\x02\xd3Q\xf3,\x89+\xa6,\xaf\t'
(2)RC4解密
脚本如下:
coding=gbk (此题密文内容超出utf-8的编码范围,要用gdk编码才能运行脚本,得到flag)
import base64
def rc4_setup(key):
"""RC4初始化"""
if isinstance(key, str):
key = key.encode()
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def rc4_crypt(data, key):
"""RC4加解密"""
if isinstance(data, str):
data = data.encode()
S = rc4_setup(key)
i, j = 0, 0
res = []
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
res.append(byte ^ S[(S[i] + S[j]) % 256])
return bytes(res)
def rc4_encrypt(data, key):
"""RC4加密"""
return rc4_crypt(data, key)
def rc4_decrypt(data, key):
"""RC4解密"""
return rc4_crypt(data, key)
def rc4_hex(key_hex, data_hex):
"""RC4加解密(16进制)"""
key = bytes.fromhex(key_hex)
data = bytes.fromhex(data_hex)
res = rc4_crypt(data, key)
return res.hex()
def rc4_encrypt_base64(data, key):
"""RC4加密并转换为base64格式"""
encrypted_data = rc4_encrypt(data, key)
return base64.b64encode(encrypted_data).decode()
def rc4_decrypt_base64(data, key):
"""base64格式解码后RC4解密"""
encrypted_data = base64.b64decode(data)
return rc4_decrypt(encrypted_data, key).decode()
if name == '__main__':
plaintext = b'\xbc\xc5\x12}\x85#\x84q{9(\x02\xd3Q\xf3,\x89+\xa6,\xaf\t'
key = b'12345678abcdefghijklmnopqrspxyz'
# RC4加密
ciphertext = rc4_encrypt(plaintext, key)
print("RC4加密", ciphertext)
# RC4解密
decrypted_text = rc4_decrypt(ciphertext, key)
print("RC4解密", decrypted_text)
# 16进制数据的RC4加解密
ciphertext_hex = rc4_hex(key.hex(), plaintext.hex())
print("16进制数据的RC4加密:", ciphertext_hex)
decrypted_text_hex = rc4_hex(key.hex(), ciphertext_hex)
print("16进制数据的RC4解密:", decrypted_text_hex)
# base64数据的RC4加解密
ciphertext_base64 = rc4_encrypt_base64(plaintext, key)
print("base64数据的RC4加密:", ciphertext_base64)
decrypted_text_base64 = rc4_decrypt_base64(ciphertext_base64, key)
print("base64数据的RC4解密:", decrypted_text_base64)
运行结果: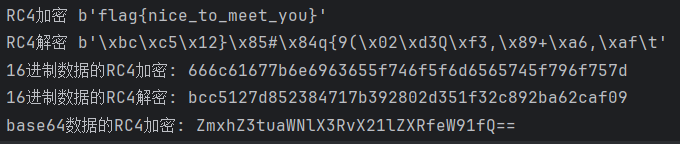
flag为:
flag{nice_to_meet_you}