一、查看文件类型
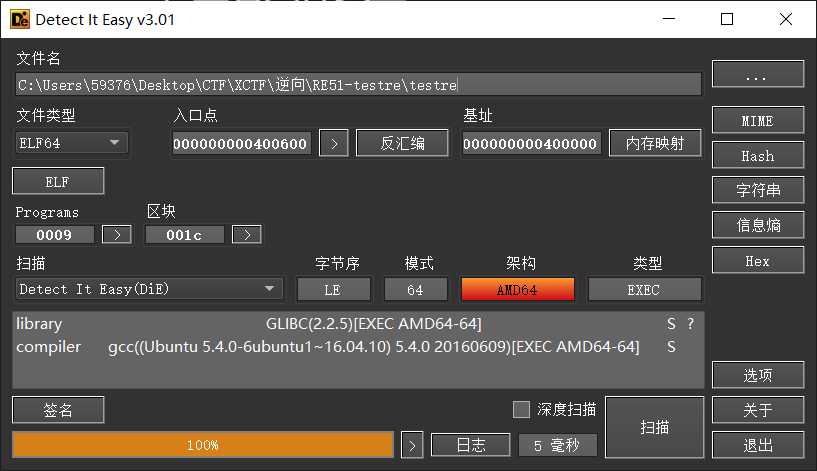
ELF64 无壳
二、IDA静态分析
1.main
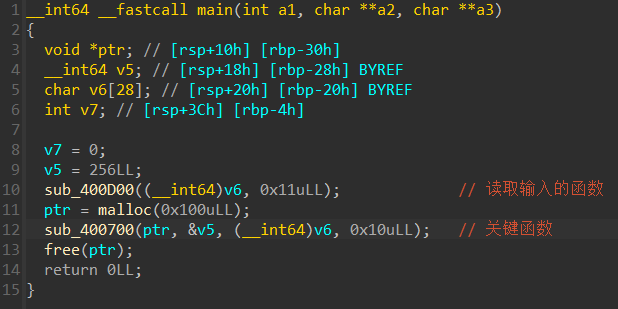
程序逻辑比较简单,只有两个调用函数
2.sub_400D00
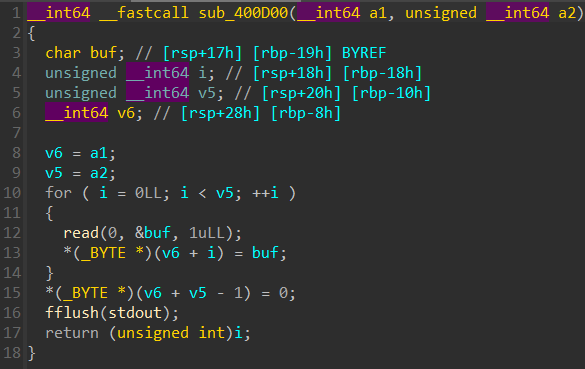
read()读取目标文件内容,fflush(stdoout)清除输出缓冲区。
sub_400D00是个读取输入的函数。
3.sub_400700(关键函数)
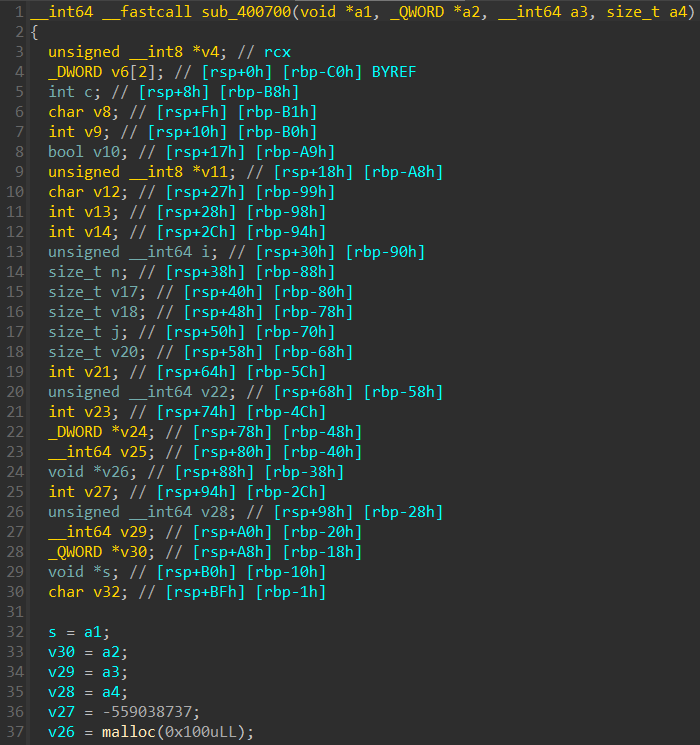
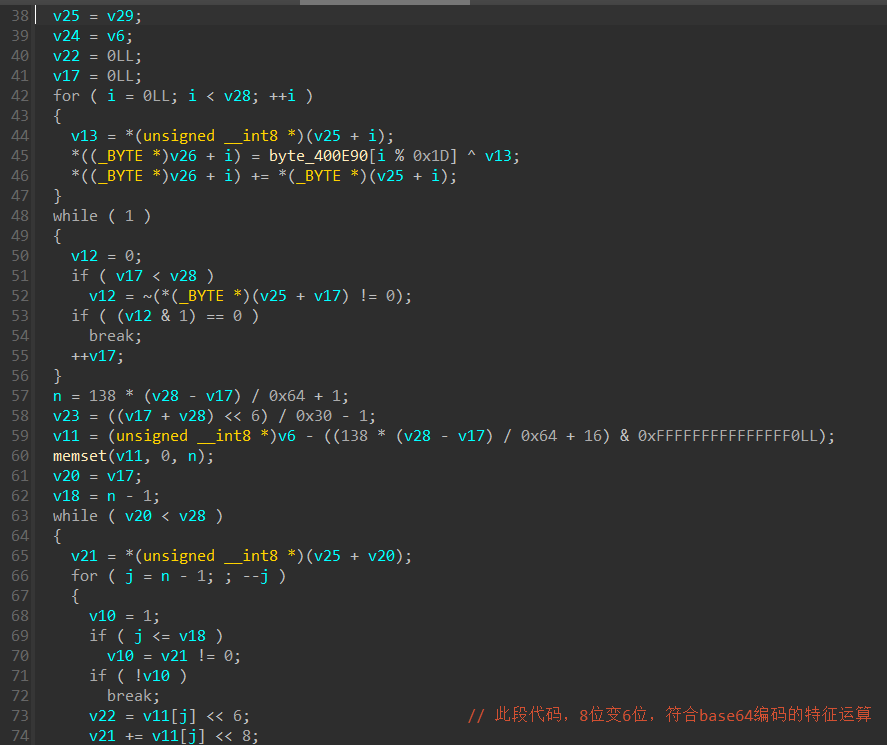
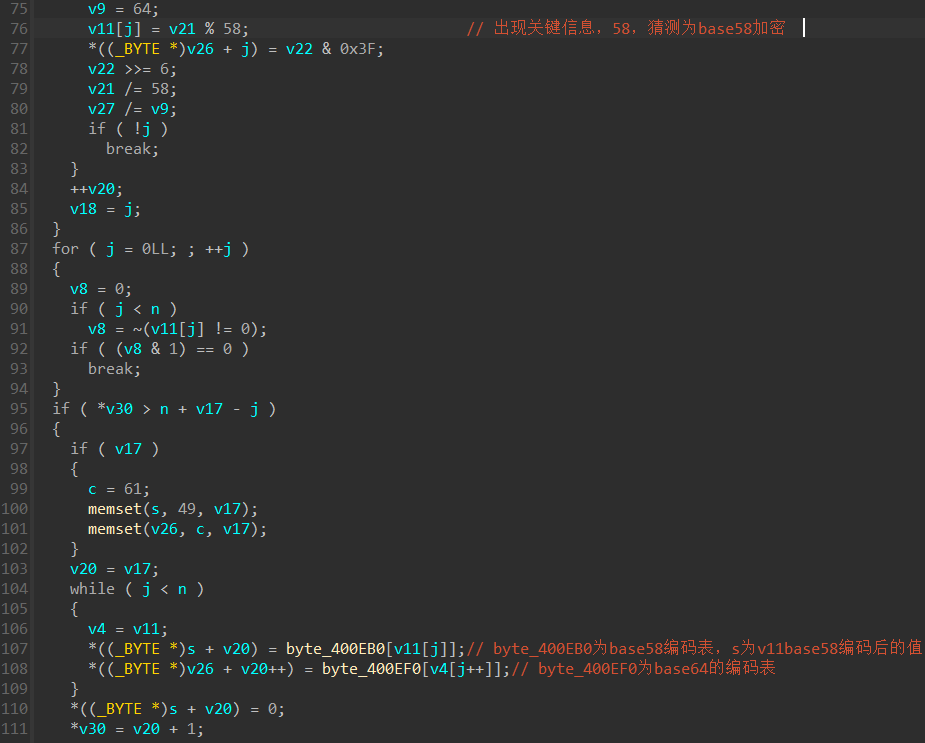
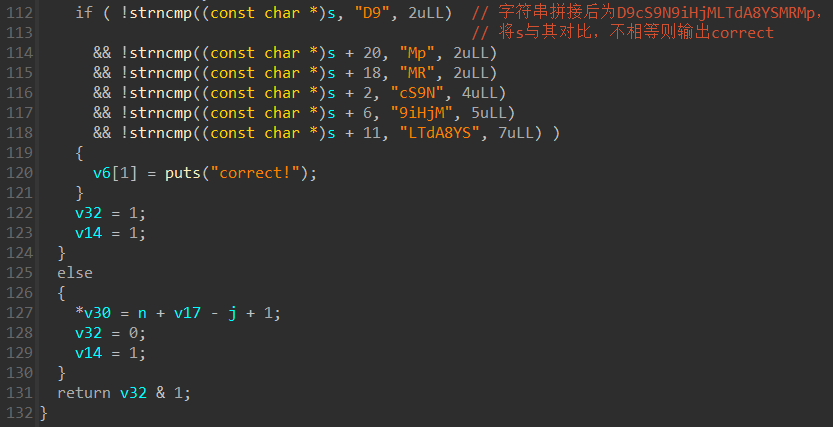
逆序分析程序逻辑:
(1)第112-118行将s与拼接后的字符串“D9cS9N9iHjMLTdA8YSMRMp”对比,相等则输出提示“correct!”
由此可知密文为:D9cS9N9iHjMLTdA8YSMRMp
(2)s来自v11,跟进第107行中对v11进行处理的循环中的数组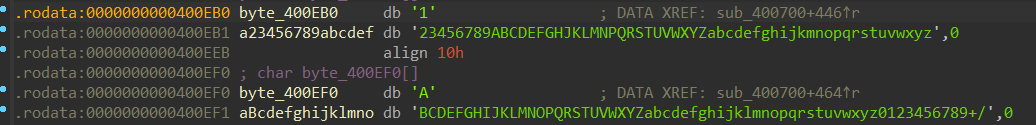
发现为base58编码表,下一行的数组为base64编码表
(3)继续往上读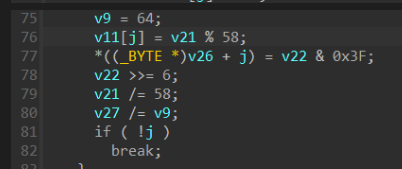
计算中出现关键数字58
确认为base58加密
三、解题
密文为:D9cS9N9iHjMLTdA8YSMRMp
(1)python脚本
def b58encode(tmp: str) -> str:
tmp = list(map(ord, tmp))
temp = tmp[0]
base58 = "123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz"
for i in range(len(tmp) - 1):
temp = temp * 256 + tmp[i + 1]
tmp = []
while True:
tmp.insert(0, temp % 58)
temp = temp // 58
if temp == 0:
break
temp = ""
for i in tmp:
temp += base58[i]
return temp
def b58decode(tmp: str) -> str:
import binascii
base58 = "123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz"
temp = []
for i in tmp:
temp.append(base58.index(i))
tmp = temp[0]
for i in range(len(temp) - 1):
tmp = tmp * 58 + temp[i + 1]
return binascii.unhexlify(hex(tmp)[2:].encode("utf-8")).decode("UTF-8")
print(b58encode("ABDCDEFGA"))
print(b58decode("D9cS9N9iHjMLTdA8YSMRMp"))运行结果:
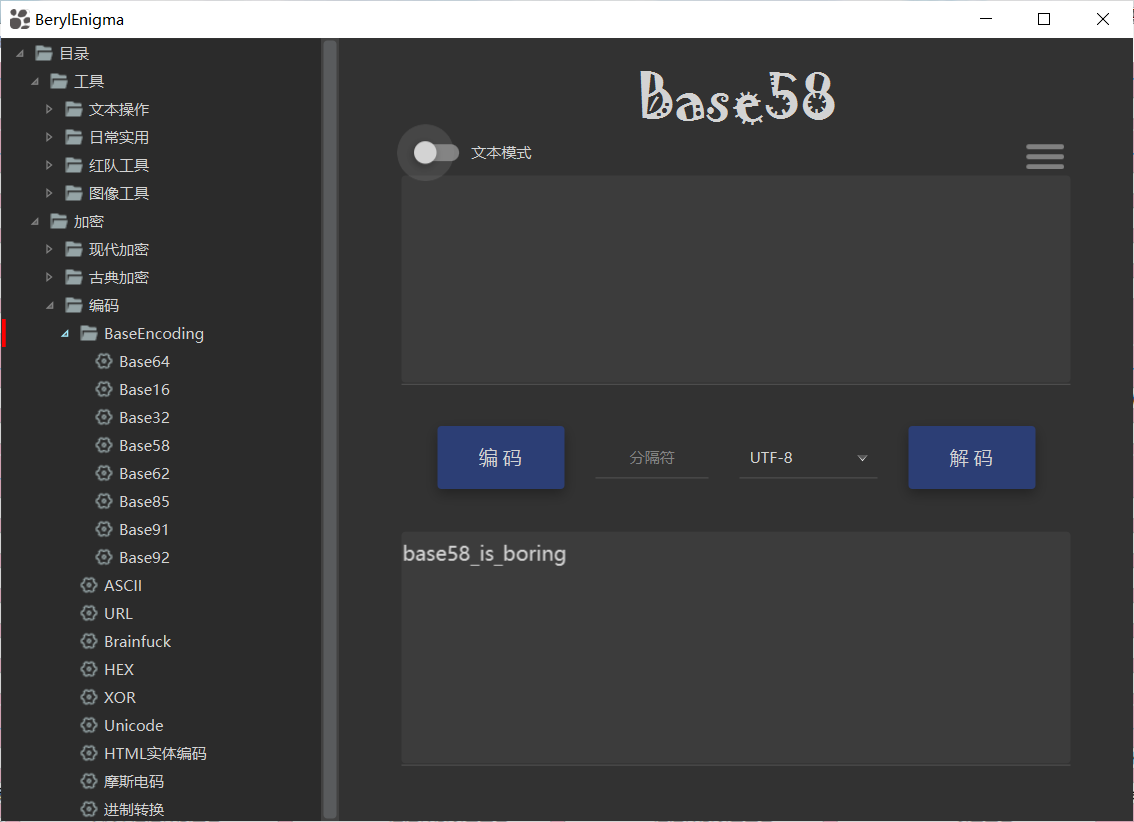
base58_is_boring
flag为:flag{base58_is_boring}
(2)本地工具箱