1.查壳
无壳 64位
2.IDA静态分析
main:
int __cdecl main(int argc, const char **argv, const char **envp)
{
int i; // [rsp+2Ch] [rbp-124h]
char __b[264]; // [rsp+40h] [rbp-110h] BYREF
memset(__b, 0, 0x100uLL);
printf("Input your flag:\n");
get_line(__b, 256LL);
if ( strlen(__b) != 33 ) // flag长度为33
goto LABEL_7;
for ( i = 1; i < 33; ++i )
__b[i] ^= __b[i - 1];
if ( !strncmp(__b, global, 0x21uLL) )
printf("Success");
else
LABEL_7:
printf("Failed");
return 0;
}程序逻辑分析:
1.将用户输入的字符从第二个元素起,每个元素与前一个元素进行异或后赋值给当前元素。
2.将处理后的输入与global比较,相等则输出“Success”
跟进变量global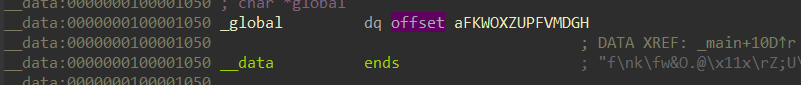
再次跟进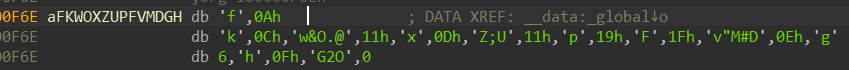
其值提取出来为:
unsigned char aFKWOXZUPFVMDGH[] =
{
0x66, 0x0A, 0x6B, 0x0C, 0x77, 0x26, 0x4F, 0x2E, 0x40, 0x11,
0x78, 0x0D, 0x5A, 0x3B, 0x55, 0x11, 0x70, 0x19, 0x46, 0x1F,
0x76, 0x22, 0x4D, 0x23, 0x44, 0x0E, 0x67, 0x06, 0x68, 0x0F,
0x47, 0x32, 0x4F, 0x00
};3.解题
将数组aFKWOXZUPFVMDGH的中的元素,从第二位起每个元素与前一个元素进行异或后赋值给当前元素,就能得到flag
第一个元素f不用异或
python脚本如下:
a=[0x66, 0x0A, 0x6B, 0x0C, 0x77, 0x26, 0x4F, 0x2E, 0x40, 0x11,
0x78, 0x0D, 0x5A, 0x3B, 0x55, 0x11, 0x70, 0x19, 0x46, 0x1F,
0x76, 0x22, 0x4D, 0x23, 0x44, 0x0E, 0x67, 0x06, 0x68, 0x0F,
0x47, 0x32, 0x4F, 0x00]
flag = ''
for i in range(1,33):
flag +=chr(a[i]^ a[i-1])
print('f'+flag)
运行结果:
flag{QianQiuWanDai_YiTongJiangHu}